Einleitung
Warning: Obtaining unauthorized access to another's computer system or systems is illegal under the Computer Fraud & Abuse Act.
The following guide was made with the purpose of educating others on cyber security tools, technologies, and techniques with the intention of educating others on better protecting their own technologies and data. Please use the knowledge gained from this guide responsibly.
This guide will demonstrate how a user can use the integrated 'Forensic Mode'
Why is this feature useful
Forensic Mode is used by security researchers and pen-testers for the explicit purpose of digital forensics. What is particularly useful about this feature is that it can be booted from a USB device containing a Kali ISO.
Booting into this mode will not mount any system hard drives, that way the operations you preform on the system will not leave any trace.
Before you begin
This guide does require you to have a Bootable USB Drive with Kali Linux written to it. If you don't already have one, you can follow this guide to create one.
=== ===
Ersatzteile
-
-
Plug in your Live Kali Linux USB into your computer and restart your PC.
-
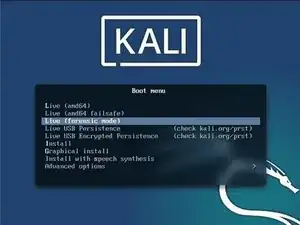
Once your machine is finished restarting you should see Kali's Boot Loader.
-
Kali's Forensics Mode can be used for the following purposes...
- Copy data from a systems drive
- Verify image integrity
- Use the included forensic tools to examine files that might cause a systems error, or recover data
Additional Information
Disclamer
The most important thing you should take away from this guide, is to remember to use this information responsibly. Obtaining unauthorized access to another's computer system or systems is illegal under the Computer Fraud & Abuse Act.
Please use the knowledge gained from this guide responsibly.