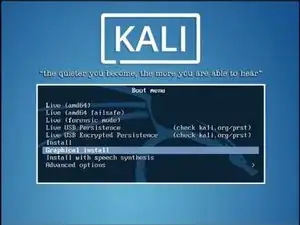
How to Install Kali Linux onto a Virtual Machine
Kali Linux is an open-source, Debian-based Linux distribution that is geared toward various cyber security tasks. Developed by Mati Aharoni and Devon Kearns, and initially released on March 13, 2013, under the Offensive Security Company as a re-write of the BlackTrack operating system. This OS was originally meant to focus on Kernel Auditing.
Kali offers around 600 penetration-testing tools and was most prominently featured on the television show Mr. Robot.
The tagline of Kali Linux is "the quieter you become, the more you are able to hear", which is displayed on some of the system's backgrounds.
Kali Linux is distributed in both 32-bit and 64-bit images for use on host devices based on the x86 instruction set. There are also images available for ARM-based processors for use on the Beagle Board computer and Samsung's ARM Chromebook.
These devices include the following computers:
Kali Linux is also officially available on Android devices thanks to the arrival of Kali NetHunter and officially supports the following devices...
and is available on more devices through unofficial community builds.
Kali Linux features a dedicated project for Android Devices named Kali NetHunter and is the first open-source Android penetration testing platform. Kali NetHunter supports the following...
Kali Linux also features a forensic mode, which was carried over from Kali's predecessor BackTrack. This feature is meant to be used with Kali's bootable USB/CD as a way to make it easy to apply for a forensic job.
When booted into the forensic mode, the system does not touch the internal hard drive or swap space, and auto mounting is disabled.
Kali Linux features some of the following security tools